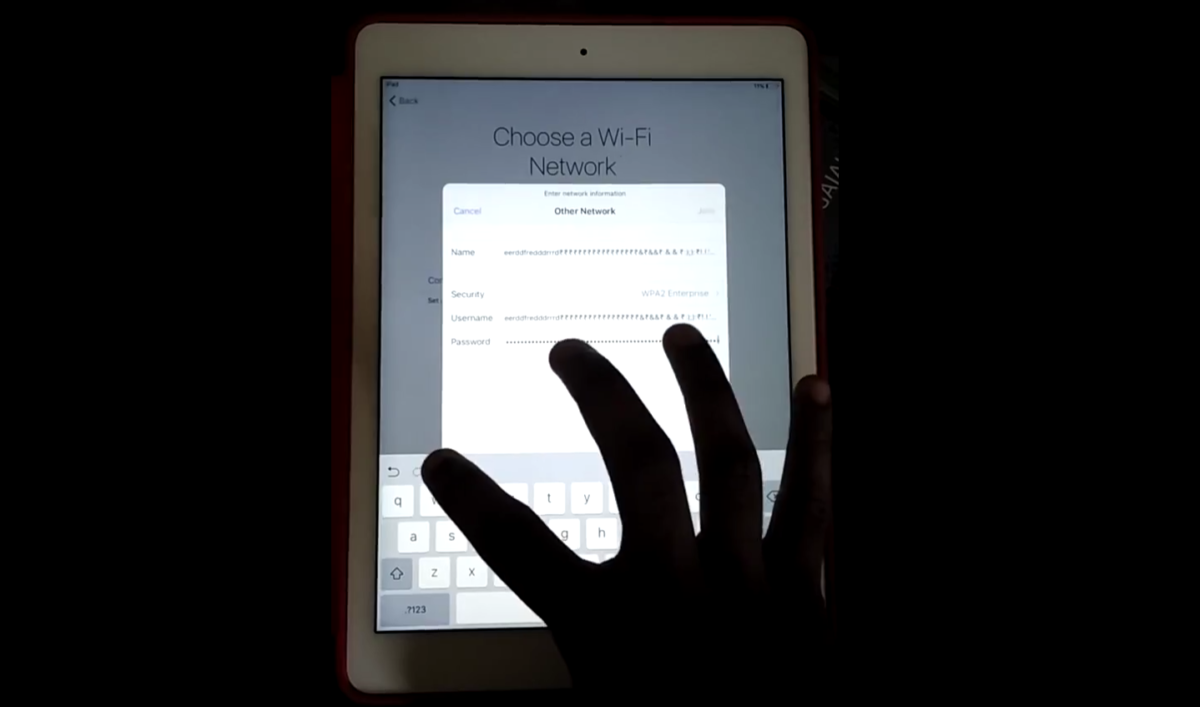
One of the strongest security mechanisms implemented by Apple is called Activation Lock. It prohibits anyone without access to owner’s Apple ID password from accessing a stolen or lost iDevice. Unless they have a lot of patience and some magnets. Read more »
Month: November 2016
New Mirai attack vector – bot exploits a recently discovered router vulnerability
Nowadays the market for IoT botnets must be really saturated. Botmasters are looking for new infection vectors to gain an advantage over competitors and a few extra Gbps of power. Yesterday one of our readers’ routers became a victim of this race. Lets look at the bot and the infection vector, which involves two vulnerabilities. Read more »
IT Security Weekend Catch Up – November 26, 2016
Afraid of missing important security news during the week? We’re here to help! Every week we put all important security related news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up – November 26, 2016”
Errors, threats and extortion – history of a bank hack part three
This is the epilogue in the Polish bank heist story, where one of the hackers gets caught by the police.
The Polish police never ceases to surprise. Another administrator of ToRepublic forum was detained by the police. This time it was Polsilver, who six months ago stole money from Plus Bank. Continue reading “Errors, threats and extortion – history of a bank hack part three”
Errors, threats and extortion – history of a bank hack part two
In this episode of the Polish bank heist we describe the actions taken by criminals after the bank they hacked refused to pay the ransom they requested.
The ultimatum presented to Plus Bank, robbed by criminals, has elapsed. The burglar, who apparently has not received the ransom, has published data of hundreds of business accounts of Plus Bank customers. Continue reading “Errors, threats and extortion – history of a bank hack part two”
Errors, threats and extortion – history of a bank hack part one
A few months ago a Polish bank fell victim to a serious hacker attack, and that its customers’ money, passwords and personal information were stolen. Within this series, we reconstruct the gradual disclosure of information on this subject.
The evidence we have received shows that a mysterious attacker had full access to the main webserver of a Polish bank for several weeks. That enabled him to make unauthorized transfers and collect personal information of customers, as well as their cards and account history. The attacker claims to have stolen a total of approx. PLN 1 million from multiple accounts, and the bank allegedly was in the dark for several weeks. Continue reading “Errors, threats and extortion – history of a bank hack part one”