This is a great story about hacking a BIOS-level locked Toshiba laptop. There will be plenty of hardware hacking, reverse engineering and perseverance. And some crypto as well.
We had the pleasure to watch this talk live at Security PWNing conference in 2017 in Warsaw. There is a recording, published yesterday, but it’s encrypted in Polish. There are also slides – this time in English, from Recon 2017 – but no recording. There’s also a partial project log – in English as well. We’ll do our best to describe what we can, but there will be moments when we can’t even pretend to understand what was happening – please refer to the slides/Hackaday entry or try to decrypt the recorded presentation. Let’s go!
How it all started
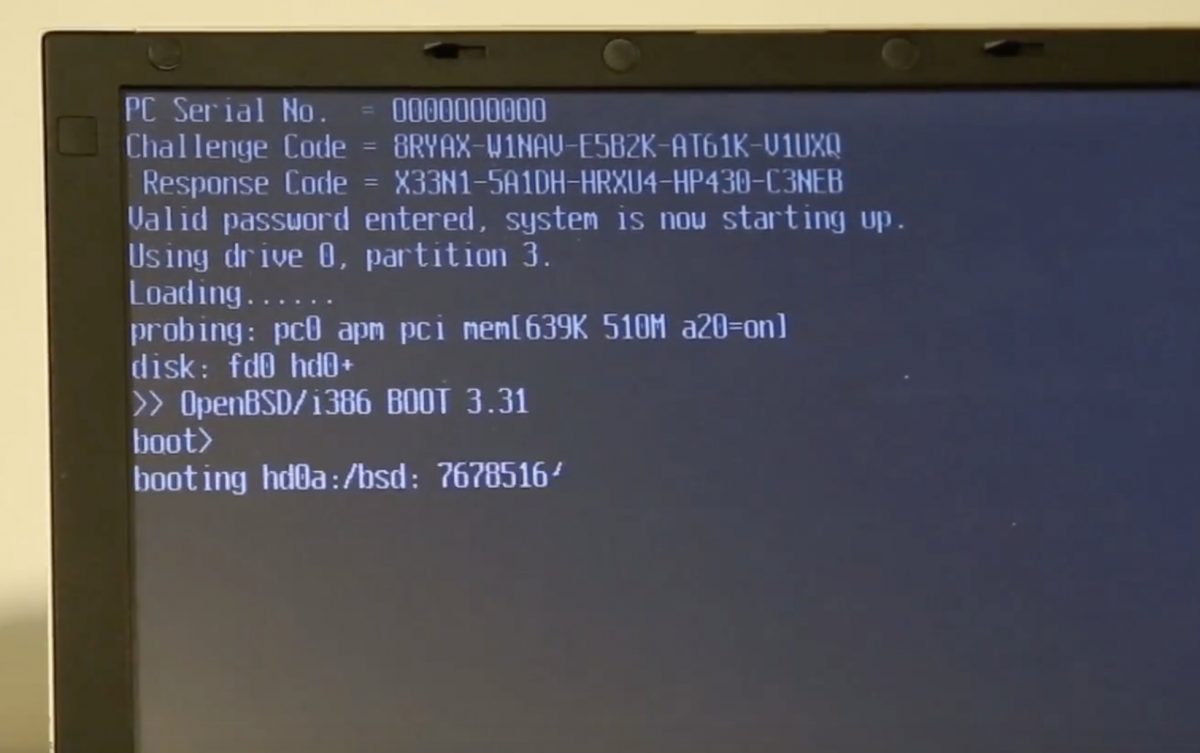
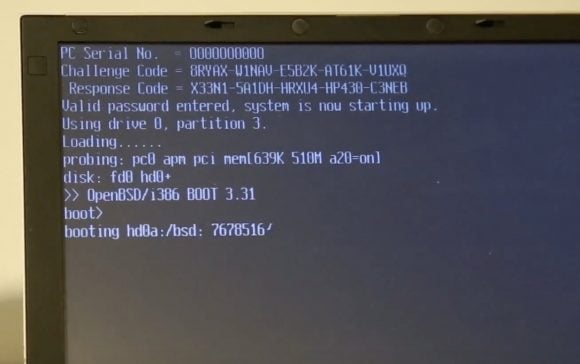
It all started with a laptop. A Toshiba Portégé R100 to be precise. Someone came to Sergiusz “q3k” Bazański asking for help in unlocking it. It had a BIOS password set up, unknown to the current owner. Sergiusz tried all the clever tricks with batteries and jumpers, but none worked. He did discover the service mode (Ctrl+Tab Ctrl+Enter) where a challenge is presented and a proper answer can unlock the machine when you lost the password, but he did not have the tool (most probably proprietary service tool made by Toshiba) to get the proper answer.
The owner soon gave up, but Sergiusz just couldn’t leave the old laptop alone. He enlisted the help of his friend Michał “Redford” Kowalczyk and they started a 3-year long journey which ended with the ability to unlock any business Toshiba laptop made between 2003 and 2017.
Geting the BIOS firmware
First they wanted to start with analysing BIOS firmware. Dumping from memory is not an option when you cannot run the OS. They did however locate a BIOS firmware update for this model on Toshiba’s website. Unpacking it was quite easy, but the image itself looked encrypted. The updater turned out to be a 16-bit one. A pain to reverse. Fortunatelly Michał was able to find a newer 32-bit updater, reverse it and identify functions that decrypted the firmware.
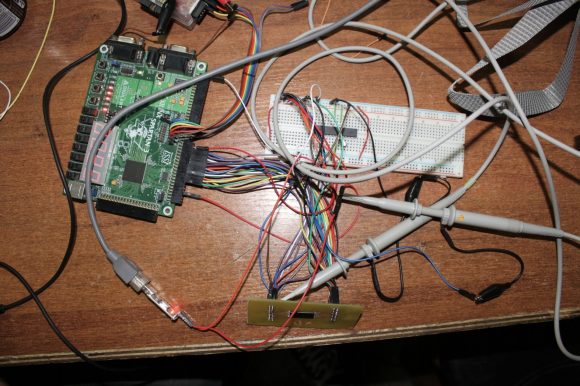
While Michał was fighting with the updater, Sergiusz tried another approach. With a heat gun, custom made circuit board, a soldering iron and lots of cables he was able to start dumping the BIOS chipset.
Dumping process was far from perfect and generated lots of errors. It was repeated several dozens times to apply simple statistics to determine which bytes were right and which wrong.
Firmware dumping ended on the very same day Michał finally decrypted the firmware update, so they were able to compare the results of their work. Only a single byte was wrong in Sergiusz’s dump.
Time to analyse
What they had was na 500 KB file where they needed to identify the part responsible for checking the password and calculating the challenge-response scheme. Michał took on the challenge. We can’t guide you through it, but involved a lot of reading of Intel manuals and learning how the boot process works inside the BIOS and memory. You can try follow Michał’s own explanation (remember, Polish) with the help of English slides (starting on slide 30).
After the necessary magic Michał located the code responsible for challenge-response mechanism. Unfortunately it turned out that all arguments are sent to a single function, which in turn sends them to a specific I/O port, which turned out to be a communication channel to a microcontroller. Further analysis showed that they have to dump another chip – this time the keyboard controller.
Second chip
This one turned out to be a much tough nut to crack. First, there were no software updates available for this laptop model. Fortunately they discovered an updater for a very similar model, Toshiba Portégé S100. They reversed the updater only to find out that the encrypted firmware was delivered directly to the controller. The controller itself was responsible for decryption, therefore the keys and algorithm never left the chip. Looks like a new task for the hardware guy.
Sergiusz had to prepare another circuit board, use his soldering skills and try to dump the firmware. It was harder than before. Much harder. He discovered that without the knowledge of a secret key dumping will be impossible. He had to find another way.
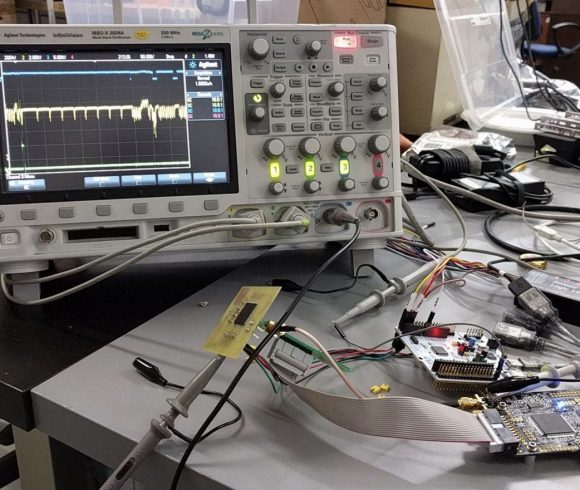
After trying a few attacks he did discover that when testing different keys sometimes the answer arrived 3 microseconds later than in other cases. It turned out that the chip was vulnerable to a timing attack. A few thousands attempts later he had the key and was able to dump the firmware. They analysed it to discover that the function to check the key did the comparison byte after byte and quit after the first failure, making the timing attack possible. See also a partial description by Sergiusz in English.
Analysis of the firmware was also hard – so hard that we are unable to describe the difficulties. Try listening to Michał (we guess your Polish is getting better every minute) or/and read the slides (starting on slide 75).
When Michał finally got to the right part of the code there was another surprise – another call to and I/O port. But this time it was an EPROM, storing MD5 hashes of user BIOS password. This was not the target of the research – they did not want to unlock a single laptop, they were looking for a generic method, so they had to go after the challenge-response algorithm.
The code they finally located was far from trivial, involved some random numbers, hardware IDs, XOR and a custom block cipher with hardcoded keys, but they were able to recreate it in Python. They also did a live demo during the presentation to show it worked. It did. Applause. A well deserved one.
They did not stop here. They had to decrypt the keyboard controller firmware update. They found the symmetric keys and checked them against a lot of firmware updates. They discovered that Toshiba did not change the encryption algorithm, nor keys, between at least 2004 and 2017. Using the very same tools they were able to unlock any business Toshiba laptop, including all recent models. Additionally, having the encryption keys, they could easily backdoor the keyboard controller. Scary.
The whole process took 3 years – but the actual work took about 2 weeks, the rest was Michał waiting for Sergiusz to dump the chips. They reported their findings to Toshiba, which promised to deliver updates and change the encryption scheme.
This is were the story ends but we hope for more from this wonderful duo. Send them your old laptops!

please help me
i have laptop toshiba with bios password