In June and July of 2015, the thieves stole several hundred thousand zlotys (at least 100k EUR) from accounts of the bank customers. The affected customers had one thing in common – they had a phone in Play network (a Polish mobile operator) and received a series of text messages with codes to authorize non-commissioned transfers.
Some time ago we met with an offender, who described how he had been robbing bank accounts of unwitting users for two months of 2015. We have verified the events described by the offender and confirmed their exact course by contacting one of the victims.
Innovative service
It all began in late 2010, when Play network offered its customers something unique on the Polish market, namely TelePlay service. The service was based on the possibility of launching a virtual phone that supported the same number as the physical phone, but through the website. Tourists and people living abroad appreciated this product – they could make and receive calls, and exchange text messages without incurring roaming charges. TelePlay was active untill approx. 20 July of 2015, when suddenly, without any explanation, the activation of new accounts was suspended and, after a few weeks, the service was completely shut down.
The termination of the service surprised even Marcin Gruszka, well-informed spokesperson of the network. Although he promised a new service, customers had to wait a bit for it. When Telefon entered the market it turned out that customers could make calls and send text messages, but without receiving them. You probably already know the reason for the termination of TelePlay. If not, you will find the answer below.
Unpleasant wake-up call
When looking for the victims, we met Łukasz, who lost few thousand zlotys on the night of June 17 to June 18, 2015. Shortly before midnight, he started receiving strange text messages. He did not hear them because he was asleep, and the next morning he saw with horror that someone draw all the funds from his account. He managed to make screenshots of his phone. It looked like this:


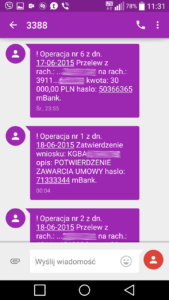
The sequence of events was as follows:
- at approx. 23:47 he received the following message TelePlay: You have just signed to TelePlay service. If this is not you, send NO to the free number 18353 (1TELE). www.tele.play.pl
- at 23:47 he received the following message: TelePlay has been enabled. Are you enabling the service for the first time? You have 14 days free of charge! Make calls from your computer! The service is automatically renewed every month for 3.65 PLN with VAT. How to turn it off? Send HELP to the free number 18353 (1TELE). www.tele.play.pl
- 23:48 transfer of 1 PLN to the account A in the same bank as the bank account of the victim (test of the criminals)
- 23:48 transfer of 1 PLN to the bank account B in the same bank
- 23:50 transfer of 30.000 PLN to the bank account B
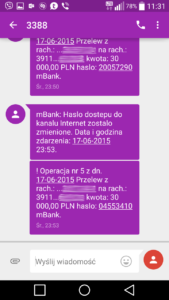
- 23:53 the password to the Internet channel has been changed
- 23:53 transfer of 30.000 PLN to the bank account B
- 23:55 transfer of 30.000 PLN to the bank account B
- 00:04 conclusion of a credit agreement
- 00:09 transfer of 39.000 PLN to the bank account C
- 00:14 transfer of 40.000 PLN to the bank account C
(40.000 PLN = around 10.000 EUR)
When Łukasz woke up shortly after 5 AM, he found out that 169 thousand zlotys was gone from his account, of which 40.000 was from the loan he did not take. He immediately contacted the bank and asked to block all transactions. It was possible to save some bank transfers made to online currency exchange websites because the criminals did not have time to convert them, but the rest was paid at an ATM. All recovered funds are still locked on accounts to which they were transferred that night.
The above course of events also fits into the scenario in which the criminals immediately pay stolen funds from ATMs. This explains 3 transfers that took place just before midnight and 2 made after midnight. A hired bogus owner could stand near an ATM and take advantage of the fact that limits of cash withdrawals are reset at midnight. It also explains the use of more than one account – with such large amounts, withdrawing everything from one bank account, even when using the daily limit twice, is not possible.
A large group of the victims
Many people who had been robbed in a very similar way in June and July of 2015 described their stories online. The same scenario repeats itself in each and every case. First, in the middle of the night, a phone within Play network, supporting authorization tokens from the bank, receives information about activating TelePlay services. A moment later, there is a wave of text messages informing about a new loan (often for the amount of several thousand zlotys), termination of deposits, and transfers to other accounts in the same bank. When distraught customers try to block transactions, 24/7 hotline of the bank accepts complaints, while their accounts are being completely cleaned. Here’s another account:
Exactly what happened to me. On 19 July, Sunday, at 20:40 (approximately) I received the same text messages. I immediately accessed the account, saw 11 thousand zlotys, changed my password and logged in again. The money was gone, the transfer had been made. Earlier, maybe 5 minutes before this event, I got a text message from Play, saying that “the service has been activated”, or something like that. Note that I did not turn on any services, I didn’t even know about the existence of this service. I immediately called the hotline, which took approximately 50 minutes, and then, at 22:00, I went to the police station to report the theft. To this day, nothing is known. everything is suspended for clarification at the Prosecutor’s Office in Białystok.
You can find other examples here, here, and here. There are a lot more of these stories. The oldest case is from June 9. We found 3 victims robbed in mid-June and 6 victims robbed from 17 to 19 July. This suggests that there are more victims out there.

How could this happen?
Step one – identifying the victims.
You probably think that emptying one’s bank account is not easy. Basically, we agree with you, but criminals are creative and with a little luck, no common sense on the part of a mobile network operator, and carelessness of users, they were able to develop an efficient and effective system of cleaning bank accounts. It looked like this.
The key to the payment of funds is taking control over the received text messages. Play operator made it much easier for the thieves through TelePlay service. To activate it, you had to send a specific text message to the indicated number, but there was also a second and easier access for the criminals, and it was Play24 website. Play customers, who established an account on Play24 and activated it with a received text message, could use the same login and password to activate TelePlay service. They did not have to send a text message or use a one-time code. All it took was a few mouse clicks and TelePlay was active. Play sent text messages about service activation, as well as text messages about signing in, but this mechanism did not disturb the criminals.
How were Play customers traced by the criminals? We heard about scanning mailboxes for messages containing invoices from Play network. Thanks to the carelessness of users, who use the same password for multiple sites, the criminals had access to thousands of logins and passwords to mailboxes. A special program reviewed their content (the so-called Barber), which identified mailboxes of Play customers, and then they were manually verified by the criminals.
Step two – infection
When the criminals knew who was the owner of a phone within Play network, they sent messages with malicious software. These messages were properly masked as invoices, information from the debt collector, or other documents that needed quick response. When the user infected his computer, the criminals were able to eavesdrop and steal passwords. That is how they got passwords to online bank accounts, where they checked the balance, as well as to Play24 website. In all scenarios, the computer of the victim was infected with malware – unfortunately, the victims played their part.
Step three – big cleaning
When the criminals had their victim and knew the login and password to the bank account and Play24 website, they activated TelePlay service. It enabled receiving text messages addressed to the victim’s cell phone on the Internet. Text messages reached the website observed by the criminals, as well as to the phone of the victim, so that the victims could see that something was wrong. Unfortunately, even an immediate call to the bank did not help with blocking bank accounts due to slow bank procedures and rapid actions of the offenders.
The criminals logged in to bank accounts and stole everything they could. They terminated deposits, took loans, and transferred all funds to bank accounts registered for bogus owners in the same bank. That is why transfers immediately reached the accounts controlled by the criminals.

Step four – big laundering
Withdrawn funds were quickly laundered. The scenarios were different – withdrawn funds could go to online currency exchange websites, used to purchase electronic goods (e.g. game codes), or paid from ATMs. Buying bitcoins was a little more complicated. It required proper preparations – apart from bogus accounts, the criminals registered accounts in different intermediaries in online payments. The criminals transferred stolen money, through services that support immediate transfers, to bank accounts registered on Paysera website (with the limit of transfers to up to 10 thousand euros) with the use of stolen scans of the documents. The website saw the transfer with the correct authorization, the bank saw the correct code from a text message, so the whole transaction took place in accordance with procedures. The funds went from Paysera to accounts on, for example. Webmoney, from where they got to cryptocurrency exchange websites, and then disappeared in BTC wallets.
Different scenario
This scenario comes from a verified story of the criminal, but we heard about other possible scenario from the banking sector. Around June 23, 2015 one of the botnets – Slave – suddenly began stealing logins and passwords to not only bank accounts, but also to Play24 website. It was a surprise to the observers, but after reading this article, you won’t be surprised anymore – the criminals could infect computers and then take advantage of the fact that some of the victims were also Play customers. It is also possible that the criminals already had a pool of stolen logins and passwords to Play24 website – they had collected them long before discovering the method (the bot stole e.g. all passwords stored in the browser) and then used them when necessary. It seems that the method of theft appeared in the criminal environment in May 2015. First thefts we discovered took place in mid-June, when first customer complaints became known to Play. But the service was terminated only after the wave of thefts from17-19 July.
What does Play say?
Shortly after our initial publication (the article was originally published in Polish a few months ago) we asked Play to answer a few questions about the case. Unfortunately, despite sending multiple questions to the spokesperson and to the press team, and despite trying to establish informal contact, we have not received any response or even information that some sort of response is being prepared.
When collecting information about the incidents, we received a link to the post on the now defunct ToRepublic forum, where in April 2014, a user nicknamed lisowy.ziom posted the following in the guidance on TelePlay service:
USE FOR SCAMS
[…] Many of you for sure thought about setting up such a service on someone’s phone number when having access to his/her phone for a short period of time (to receive two one-time codes for registration and activation). Getting one-time codes can be done by using sociotechnics (or clever phishing). Unfortunately, the user receives a text message about activation of the service. […] Imagine… insight into all text messages, billings, ONE TIME CODES FOR BANK TRANSACTIONS, sending text messages (e.g. premium, blackmailing) without the knowledge of the user, or conversations at his expense. […] The whole thing can be performed at night (assuming we have the password and login to the bank) – the victim is asleep, we log in to TelePlay – the victim gets notification on the phone, but is still asleep 😉 and we act by taking all one-time codes to appropriate services and using them before the victim wakes up. The only problem is that the sound of a text message may wake up the victim.
This means that, despite the risks associated with Telepay were known even to the criminals, Play did not secure the activation procedure. When Łukasz, whose story we described above, filed a complaint to Play in June, in response he found out that his claim would not be considered because the service was free of charge for 14 days, therefore there were no grounds for the complaint. Play also refused to turn off TelePlay activation in the future.
Who is to blame?
We will try to be brief, because longer considerations are the task of lawyers. Without a doubt, the criminals who robbed accounts are guilty. On the other hand, Play seems to be guilty as well. The company designed the service of receiving text messages in such a way that it could be activated without the knowledge of the customer. Customers are also guilty, because they infected their phones with malware. Banks are guilty as well, because, in the middle of the night, they granted big loans, but were not able to detect anomalies associated with emptying the account or block the transaction immediately after notification from the customer. The role of the telecommunication operator and the bank is greater because these entities had the knowledge that could prevent the fraud. It will be a tough nut to crack for the court, customers may never see their money, and the criminals are seeking additional ways of defrauding the system.
After several days Play finally responded, but did not inform us about the response, so we had to find it ourselves. For 8 days the spokesperson was not able to write an e-mail, but the publication of the article has helped. Of course, there was no information about why such a critical service was not properly secured, but the following passage is our favourite:
PS: I wonder also why this text appeared just last night? Strange coincidence.
Apparently we are taking part in the so deep conspiratorial conspiracy that even we do not know what’s going on.

