Afraid of missing important security news during the week? We’re here to help! Every week we put together a curated list of all important security news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up – January 13, 2017”
IT Security Weekend Catch Up – January 7, 2017
Afraid of missing important security news during the week? We’re here to help! Every week we put together a curated list of all important security news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up – January 7, 2017”
IT Security Weekend Catch Up – December 31, 2016
Afraid of missing important security news during the week? We’re here to help! Every week we put together a curated list of all important security news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up – December 31, 2016”
IT Security Weekend Catch Up Holiday Edition – December 25, 2016
Afraid of missing important security news during the week? We’re here to help! Every week we put together a curated list of all important security news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up Holiday Edition – December 25, 2016”
Simple DIY real-life malware analysis
Instead of targeting wide audiences, some malware campaigns prefer to fly under the radar. And sometimes they fly straight into the hands of our BadCyberLab analysts, where they are dissected and analysed. Read more »
IT Security Weekend Catch Up – December 16, 2016
Afraid of missing important security news during the week? We’re here to help! Every week we put together a curated list of all important security news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up – December 16, 2016”
IT Security Weekend Catch Up – December 9, 2016
Afraid of missing important security news during the week? We’re here to help! Every week we put together a curated list of all important security news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up – December 9, 2016”
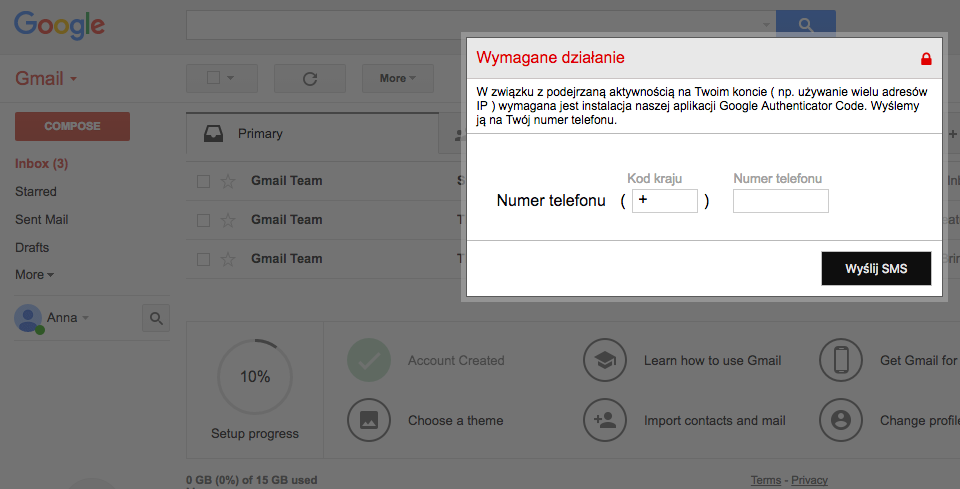
Banking trojan, Gmail webinject, SMS message and malicious APK – all in one attack scenario
As many banks use SMS 2FA for transfer authorization, malware authors are constantly looking for new opportunities to take over control of PC infection victims’ smartphones. We have identified a new attack scenario that involves both PC and mobile devices infection by leveraging trust people have in Google services. Continue reading “Banking trojan, Gmail webinject, SMS message and malicious APK – all in one attack scenario”
IT Security Weekend Catch Up – December 2, 2016
Afraid of missing important security news during the week? We’re here to help! Every week we put together a curated list of all important security related news in one place, for your reading pleasure. Enjoy! Continue reading “IT Security Weekend Catch Up – December 2, 2016”
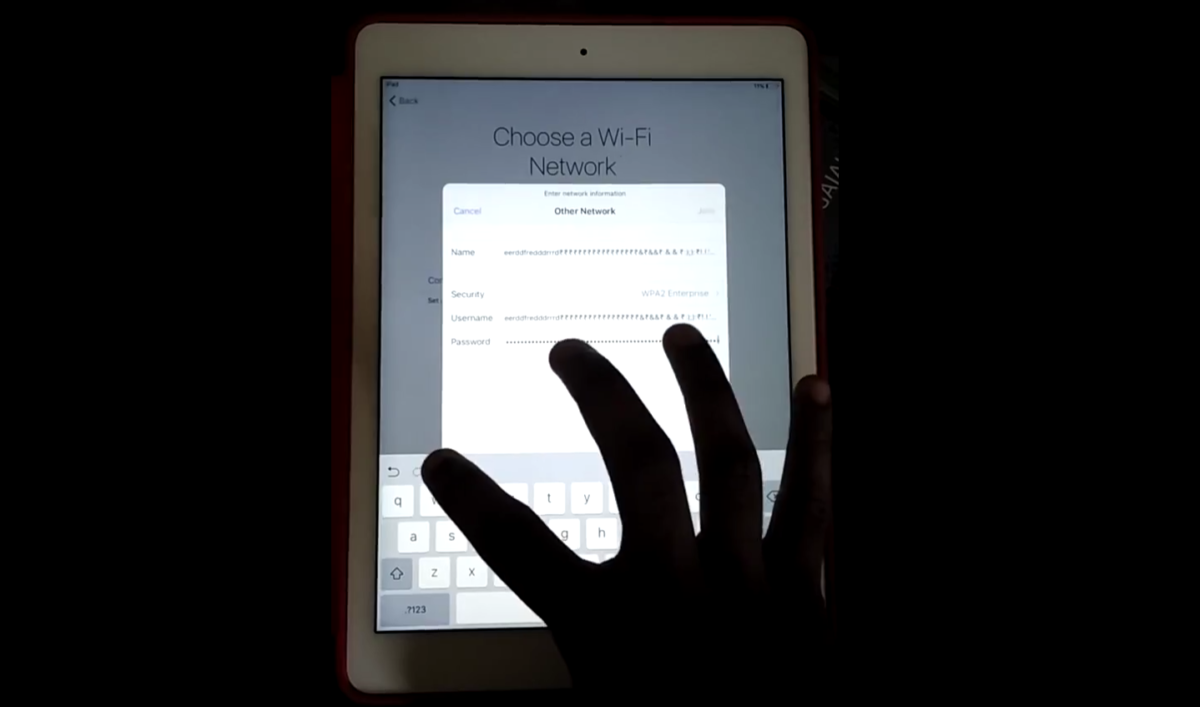
Bypassing Apple’s Activation Lock with typing and magnets – for a fraction of a second
One of the strongest security mechanisms implemented by Apple is called Activation Lock. It prohibits anyone without access to owner’s Apple ID password from accessing a stolen or lost iDevice. Unless they have a lot of patience and some magnets. Read more »