The evidence we have received shows that a mysterious attacker had full access to the main webserver of a Polish bank for several weeks. That enabled him to make unauthorized transfers and collect personal information of customers, as well as their cards and account history. The attacker claims to have stolen a total of approx. PLN 1 million from multiple accounts, and the bank allegedly was in the dark for several weeks.
This is a three-part story. You are reading part number one. Here are the links for part two and part three.
For two months, since we identified the bank in question, we cooperated with them. At the bank’s request, we met its representatives, shared our experience and knowledge about similar cases and the Polish Internet underground, and shared all we know about the information leak. After days of waiting, we received the bank’s official position. We also sent them the article we were going to publish. A few hours before the publication, the legal counsel representing the bank sent us a cease and desist letter. Days later, we had an anonymous threat suggesting that a contract for the article author could be made. For the reasons we will discuss later in the article, we have decided not to disclose the name of the bank.
To make the story credible, the attacker has shown us the full information about several hundred payment cards, the personal information of a thousand customers, ten thousand mobile phone numbers of customers, the logins and passwords of 150 customers and their account balance (most of which were in excess of PLN 100,000), thousands of items from statements of customers’ accounts, transfer confirmations for hundreds of thousands of zlotys, allegedly stolen, and a copy of the bank’s webserver along with a part of its e-banking system. Read on to learn the full story.
According to the bank, attack attempts did take place and they were detected, and the customers’ money is safe. However, the bank refused to answer detailed questions, citing legal and security considerations.
100 payment card details for starters
For us, the story began on 10 April 2015, when we received the first email from the attacker, sent from [email protected], including the numbers and holders of 100 payment cards. The nature of the data suggested they had been taken from the database of a specific bank.
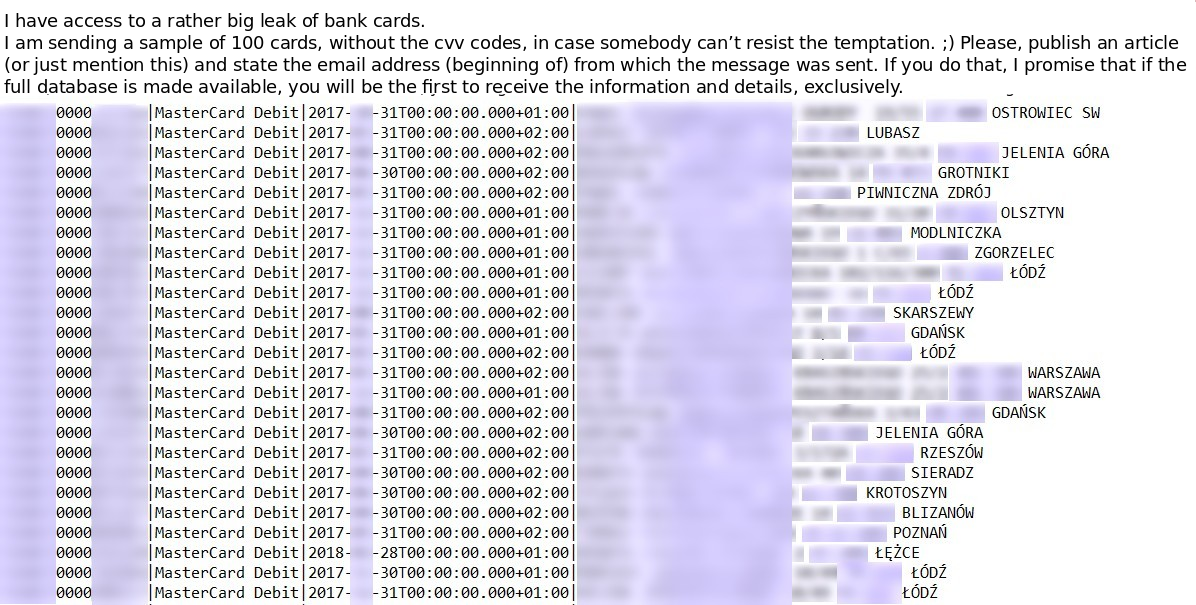
We paid particular attention to several things on the list. First, all the card numbers had the same IBAN identifier, which indicated a Polish bank (we can only say it is a commercial bank from outside of the 10 largest banks by assets). Second, it did not seem like the data had been stolen from chain stores or ATMs. The customers were based throughout Poland, some of them having two cards listed; the list also included cards of people with the same last name and residence address. All of that suggested the information originated from a bank’s system.
Using private channels we contacted the bank, which officially confirmed they knew about the problem. We replied to the email sender and waited. Despite ongoing communication with razor4 and the bank, neither party provided us with anything that would give us a better grasp of the situation. We only knew that razor4 demanded ransom from the bank for not publishing the data.
Cards on the table
In the next days, razor4 sent us more stolen data and a lengthy description of his actions. He claims to have accessed the bank’s servers in late January by exploiting an undisclosed error caused by failure to apply regular software updates.
According to the attacker’s information, after making a reconnaissance and preparing suitable bank accounts, he started to steal money from the bank’s customers. This was done by modifying the bank’s website to call a JavaScript on the attacker’s server, which allowed him to replace the target account numbers for money transfers with the attacker’s account numbers. Specifically for that purpose, razor4 registered a domain which was just one letter off the bank’s actual domain.
We have also seen the JS script the attacker used for automating attacks against the bank’s customers. In our opinion, the script looks very reliable.
Razor4 claims to have stolen several thousand zlotys in a week, and to have made a single transfer for almost PLN 180,000 on 16 February 2015 originating from a Warsaw-based car dealership. According to the attacker, the bank blamed Trojans on customers’ computers. As a matter of fact, the bank reminded its customers of transaction security a few days later (note, however, that all banks carried out similar awareness campaigns this year).

Alleged errors in the bank’s systems
Razor4 claims to have adopted another method at that time, as he had discovered a serious error in the transfer authorization system: if customer Smith defined a trusted recipient Jones, then customer Williams could transfer funds to Jones without entering an SMS confirmation code. That way after adding trusted recipients on one account under his control, razor4 could make transfers to pre-defined accounts of the trusted recipients without authorizing them with SMS codes. To that end, he set up a script on the bank’s server to save user logins and passwords and, having identified the account or a hotel located in a popular seaside town with a balance of approx. PLN 700,000, he launched the attack. According to his story, he virtually emptied the hotel’s account within a few hours one Monday. Having noticed that something was wrong, the account owner managed to block some of the transfers, and the bank resolved the error within 2 days. To prove that, razor4 has shown us the account statement:
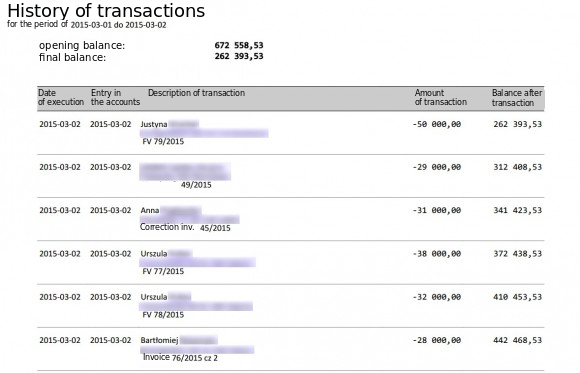
Razor4 suggests that even though the bank used password masking, he could easily intercept passwords over several login sessions. He also claims that the bank enabled the masked field to be randomly selected during login, which made it easier for the attacker to use the characters he had obtained. Indeed, the account login mechanism of the bank selects another random character set on each attempt, so given a certain number of attempts, you could get a set matching the characters you have intercepted. The evidence we have received also includes almost a hundred of complete or near-complete passwords of the bank’s users.
The third attack allegedly committed by raor4 involved an attempt to swindle approx. PLN 3 million. First, he targeted customers with two accounts, where one account was seldom used, to clone them in other banks (by making a transfer with a specific title, you can open an accounts in another bank). Then he found out that by modifying one of the parameters passed by the bank application it was possible to bypass transfer authorization with SMS codes. He targeted high-balance accounts that were rarely used and generated multiple transfers over one night, but the bank must have found out that something was wrong, blocked access to the transaction system for all customers and removed the intruder from the system. We have no evidence for that attack, but these events were partly confirmed by the bank’s customers, who complained in social media that the transaction system was unavailable for 2 days.
The fourth episode of the story involved the use of customer logins and passwords. Razor4 claims they enabled him to steal money from the account of a company offering quick money transfers between banks and handling online payments. He generated transfers to its internal accounts, opened specifically for that purpose. That way, razor4 claims, he managed to steal another PLN 30,000. The company in question has confirmed funds were stolen from its account due to the bank’s fault.
Proof of access to the server
The attacker has shown us a server catalog listing to prove he had access to the bank’s webserver. Based on the listing analysis, it can be assumed that razor4 is very likely to have had control of the banks webserver. The listing is almost 5 megabytes and mainly includes a complete file list of multiple Weblogic application server instances, where file paths are consistent with the files available in all the available versions of the bank’s e-banking website. The file listing also includes traces of the attacker’s activity. Of course, they might have been fabricated, but the list seems very credible.
For instance, the following gem can be found in the listing:
-rw-r----- [xxx]/[xxx] 3905 2013-07-08 20:49 [xxx]/xxx/xxx/xxx/xxx.png -rw-r----- [xxx]/[xxx] 2359902208 2015-03-04 13:35 [xxx]/xxx/xxx/xxx/k.tar -rw-r----- [xxx]/[xxx] 676 2013-07-08 20:49 [xxx]/xxx/xxx/xxx/xxx.jpg
‘xxxx’ server is a mobile instance of the electronic banking interface. It includes a catalog with graphic files from 2013 with a 2-gigabyte file named k.tar, created on 4 March 2015 at 1:35 pm. The listing was probably created on the same day at 4 pm. The k.tar file seems to be an archive including the whole file system and available for download from the bank’s webserver. Naturally, the file has been removed, but the other paths are still working.
The attacker has also presented us with the server’s configuration files and a copy of the e-banking application. This confirms that the attacker had the right to read, create and modify files on the bank’s webserver that handled customers’ operations.
Razor4 also claims to have stolen information about some of the bank’s customers. To prove this, he has submitted 25,000 entries from the transaction history of various accounts, the personal information about 1,000 customers, including their full names, phone numbers and email addresses, and the details of approx. 600 payment cards, 10,000 phone numbers allegedly owned by the bank’s customers, and well over a hundred logins and passwords to their bank accounts.
All the events described above are probable from the technical point of view. The attacker’s story is consistent and we have identified no contradictions or significant gaps. Some of the attacker’s claims are also backed up by evidence from independent sources (information from an affected company, false bank domain, customer complaints about e-banking service unavailability).
The bank’s reaction
After a long wait, we received the bank’s official position on the matter. See below for its most important fragments. In our opinion, not a single sentence denies the events we describe; there is not a single statement confirming them, either.
In the first quarter of this year, [bank’s name] identified attempted hacker attacks. Thanks to our security systems and actions undertaken by the Bank’s security services, the attacks were detected and, most importantly, all the funds of our customers were and are fully safe. The bank has reported the illegal activities to and continues to cooperate with relevant law enforcement authorities, including the Police and the Prosecutor’s Office. […]
In connection with the questions submitted to [bank’s name], we would like to point out that all the correspondence in question originates from an individual who plans to attack the Bank’s public image illegally and in violation of law. Any such actions are and will be reported to law enforcement authorities.
With regard to the detailed data included in the correspondence in question, given the applicable regulations of law and the security of the Bank’s operations, [bank’s name] is not authorized to disclose any information or make any public statements about the security features protecting its information systems and the data of its customers.
We stress that the funds of the Bank’s customers are safe, and the bank systems are properly secured.
The last sentence in particular suggests that even if money was indeed stolen, the bank has covered any losses.
Demands and threats
A week ago, 5 days before the planned publication date (postponed several times at the bank’s request), we received a cease and desist letter, which included the following passage:
[…] I demand that you refrain from spreading information about the effects of the hacker attack attempts against the ICT system of the Bank and the resulting security measures undertaken by the Bank […]. The information is based on unreliable sources and does not take into account the Bank’s position on the matter. Spreading said information will constitute openly and self-evidently unlawful behaviour damaging the Bank’s interests (reputation) and resulting in losses which would be difficult to compensate.
Around 11 am on Friday, the following message was send via our contact form from the IP address
37.147.97.33:
Hi sweetie, let me just say you’re already in our way, so you’d better think twice before publishing the article about the [bank’s name] attack, 20k is not so much after all, and your head falls, want to get what’s coming?
Best regards
Only a small group of our trusted associates, the attacker, and the bank knew about our plans to publish the article. We do not know the author of the message. We could discuss its meaning for a long time and see it as nothing more than hollow threats, but everyone has their acceptable level of risk, and our level has been exceeded in this case. At the same time, we think that the bank’ customers deserve to be notified of this uncommon incident, so they can change their passwords (not just bank passwords) and review their transaction history. The attacker also threatens to sell the stolen information or make it publicly available, and hence our decision to publish the article, even if some details need to be omitted.
I am a customer, what should I do?
Unfortunately, we cannot narrow the group for which these instructions are intended, but we believe that everyone will benefit from them, regardless of whether they have been affected by the attack. So if you logged into your bank system (web-based or mobile) this year, and your bank is not ranked among the largest ones, the first thing you should do is change the passwords to your bank accounts. If you use the same password to other resources (email, another bank), change it there as well, and preferably choose another password than your bank password.
After you change the passwords, take a close look at the history of all your transactions on all your accounts in 2015. If you find any unaccountable items, consult this with your bank. You should pay particular attention to two types of transactions:
- large transfers to unknown accounts,
- transfers with strange titles (such as ‘account opening’, ‘account opening confirmation’) for PLN 0.01, PLN 1.01, and similar amounts.
If you notice such items, they might have been caused by something else than your infected machine.
Review your card transactions as well. If you find any suspicious entries, consider cancelling your existing cards and requesting new ones, as the attacker may be in possession of your full card information.
After you complete these steps, we still recommend added caution. While the bank seems to have gotten rid of the intruder, criminals may still have your leaked personal and contact information, and may attempt to resell it. They might also try to use it to take out loans in your name or trick you to share other details by email or phone. Be alert and review your statements regularly. Checking your credit report may also be a good idea.
Read second part of this story here.
